Vulnerability Analysis, Detection, and Defense of Firmware for IoT EndpointsNEW
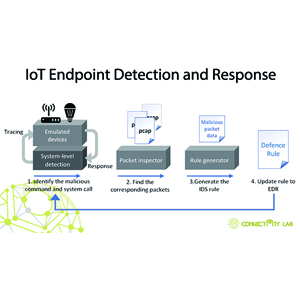
Due to the limited computing power and operational interface of IoT endpoint devices, few system-level active defense mechanisms can be developed and applied. By rebuilding the firmware on simulated peripheral hardware, we can implement highly realistic shadow simulation endpoints for IoT endpoints to be protected, and realize system-level monitoring, anomaly detection, and subsequent defense on simulated and software-based endpoints. The mechanism and platform of this achievement can be physically applied to the IoT environment, greatly improving the security of IoT devices, increasing the public's trust in IoT applications, and promoting the widespread use of IoT applications. In order to identify and prevent malicious attacks on IoT endpoints with limited computing power, this achievement rebuilds IoT firmware through symbolic execution automation on simulated peripheral hardware, and creates highly realistic shadow virtual endpoints for the entity endpoints to be protected. Through system-level monitoring on the shadow endpoints, it can identify system-level attack behaviors and corresponding malicious packets, and then use IDS to block malicious packets to protect the entity endpoints, achieving IoT endpoint detection and response (EDR).
CYBERSEC 2023 uses cookies to provide you with the best user experience possible. By continuing to use this site, you agree to the terms in our Privacy Policy .